Blogs
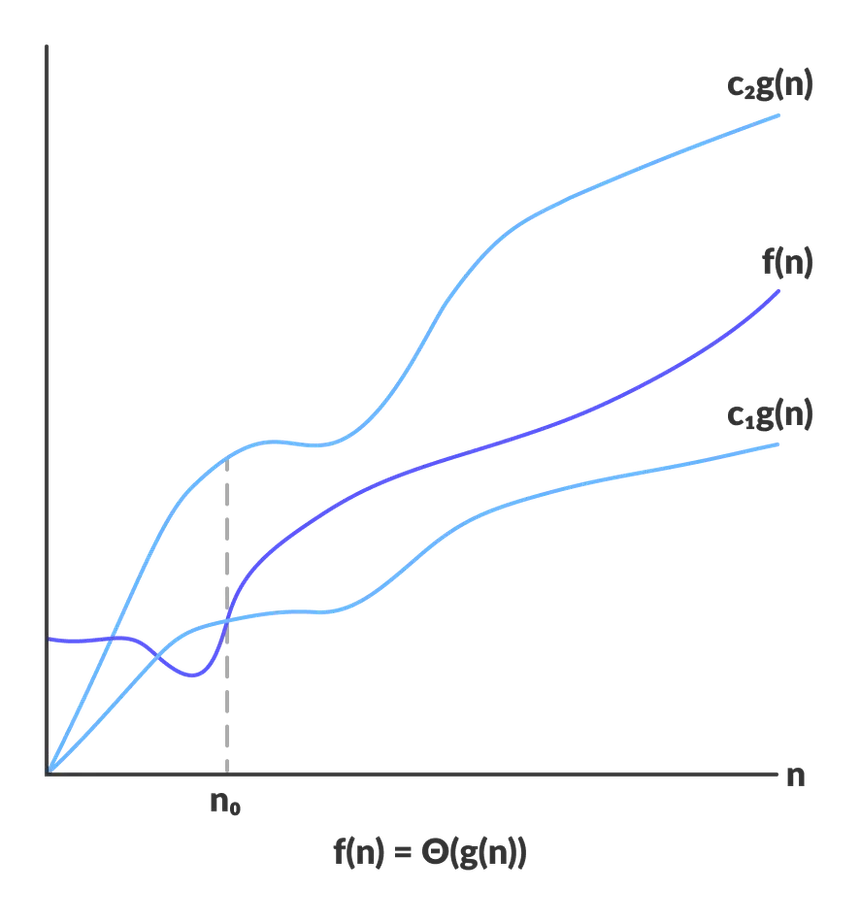
Asymptotic Analysis: …
Introduction
Recently, a friend who is considering a career shift to software engineering sparked a conversation about algorithms and the analysis of runtime complexity. This friend is naturally curious, often asking “why” to understand new concepts—an admirable habit that many could …
Public-Key Cryptography: …
Public-Key Cryptography
Public-Key cryptography works by using pairs of mathematically related keys generated by cryptographic algorithms. These cryptographic algorithms are based on difficult ( one-way ) mathematical problems, such as the discrete logarithm assumption. In other words, the …
Reverse Engineering: An …
Learn about Linkers
Whether your interested in low-level development or reverse engineering malware, understanding how linkers work and being able to write your own linker script is an important skill.
I recently created a gitbook, that will elaborate on several important linker topics, such as: …